Category: Software development
Software Development Life Cycle SDLC
In this article, we will explore the different types of SDLC models and the advantages and disadvantages of each one, and when to use them. So V-Model contains Verification phases on one side of the Validation phases on the other side. Verification and Validation phases are joined by coding software life cycle model phase in V-shape. Building Security In Maturity Model – Measure and benchmark your software security program against other security programs and industry best practices. The best method for ensuring that all tests are run regularly and reliably, is to implement automated testing.

After testing, the overall design for the software will come together. Different modules or designs will be integrated into the primary source code through developer efforts, usually by leveraging training environments to detect further errors or defects. It can be used with any type of project, but it needs more engagement from the customer and to be interactive. Also, we can use it when the customer needs to have some functional requirements ready in less than three weeks and the requirements are not clear enough. This will enable more valuable and workable pieces for software early which also increases customer satisfaction. Verification and validation of the product in the early stages of product development.
Phase 7: Maintenance
In this method, the requirement has to be precise like what kind of operations will be done, how it will be done, in which currency it will be done, etc. It improves the collaboration between the project team and all the stakeholders. Let’s get started and learn about types of SDLC and their processes. DbForge Studio comes with an advanced entity-relationship diagram design tool aimed at designing database schema diagrams and visualizing your database as an Entity Relationship Diagrams . DbForge Database Diagram Designer combines Database Diagram, Database Modeling, and Table Designer utilities to help you effectively perform various database tasks.
As the complexity and scale of programming grew, the concept of structured programming emerged. Over time, structured programming demanded more tactical development models, thus sparking the beginnings of the SDLC. One of the most flexible SDLC methodologies, Spiral takes a cue from the Iterative model and its repetition.
Related Products
This design focuses on those aspects of the software that will be visible to the user. The customer then checks the prototype, and any modifications or changes that are needed are made to the prototype. In this type of SDLC model testing and the development, the step is planned in parallel. So, there are https://www.globalcloudteam.com/ verification phases on the side and the validation phase on the other side. Once when the client starts using the developed systems, then the real issues come up and requirements to be solved from time to time. Before creating a product, a core understanding or knowledge of the product is very necessary.
Every testing included in this model verifies the software as per the requirements validated by the clients. You have to perform all the resource, cost, and time-related analyses at this step only; otherwise, your project can face non-preventive risks in the future. Once you are done with all the planning and ready with your project charter and other crucial plans, you can initiate the designing phase. Deployment is a set of PowerShell scripts that helps to integrate automation into your workflow.
Software Engineering | SDLC V-Model
The agile model is centered around the iterative and incremental approach and cross-functional teams work in collaboration. The project does not follow a downward trend towards completion. Instead, the process turns upwards after the development phase and testers use the test plans created earlier to evaluate specific components of the product. The shift starting from the development phase allows forming a typical V-shape.
The development of a software product would not be systematic and disciplined if a precise SDLC model is not used. When a team produces a software product, team members must grasp when and what to do. Otherwise, it would be an indication of turmoil and project failure.
SDLC Phases
Each model has a unique set of actions that ensure the development process’s success. We hope this article sheds more light on various SDLC models available. They are focused on the deployment of software for regular use. These processes need to enable users to work with the software and provide ongoing technical support when necessary.
- In the end, these prototypes are combined to present a complete software solution.
- The internal design of all the modules of the proposed architecture should be clearly defined with the minutest of the details in DDS.
- However, unlike traditional software development that addresses security as a separate stage, SDLC addresses security every step of the way through DevSecOps practices.
- As such, the steps implemented lead to the creation of the final product.
- The coding phase includes system design in an integrated development environment.
- This model has a strict plan and like in a waterfall model, the next stage doesn’t begin until the previous one is finished.
Some will argue that the SDLC no longer applies to models like Agile computing, but it is still a term widely in use in technology circles. The SDLC practice has advantages in traditional models of systems development that lends itself more to a structured environment. For example, the waterfall model is famous for its simplicity, as the development process in this model is linear and each phase begins only after the previous one is completed. However, it requires excessive research, and any change in a later stage will ultimately affect the completed ones. It includes steps to follow for each stage, and each stage must be completed before moving on to the next one. It is developed to overcome the weaknesses of the waterfall model.
Get the latest news, tips, and guides on software development.
It represents all of the procedures required to move a software product through the stages of its life cycle. It also captures the structure in which these procedures will be carried out. In other words, it maps the many actions performed on a software product from its inception through its retirement. The SDLC consists of clearly defined processes for creating software. It provides detailed stages for the quick development of software. It states the design phase for the stages involved in product development.

This need for greater software security comes at a time when there is tremendous pressure on developers to build better applications faster than ever andmodernize those appsfaster, too.. As a result, development teams are turning to more agile processes to further streamline workflows and reduce time to market. This is a big reason why companies are implementing a DevSecOps approach that looks at the entire SDLC and integrates security testing from beginning to end. While there are multiple SDLC models (waterfall, agile, iterative, etc.), many companies have, or are transitioning to, a DevOps model. When security is integrated as part of this process, it is referred to as DevSecOps, Secure DevOps, or sometimes as theSecure Software Development Lifecycle . In the SSDLC, security processes are implemented in all stages of the development life cycle.
Software Development Life Cycle Model
It’s crucial to have a plan for collecting and incorporating stakeholder input into this document. Failure at this stage will almost certainly result in cost overruns at best and the total collapse of the project at worst. Once the product is tested and ready to be deployed it is released formally in the appropriate market. Sometimes product deployment happens in stages as per the business strategy of that organization. The product may first be released in a limited segment and tested in the real business environment (UAT- User acceptance testing).
Solution Architecture Roles and Responsibilities Explained
They are the ones who oversee the successful implementation of the quality solution. Therefore, they have to possess a clear understanding of the client’s vision and goals to achieve productive and effective outcomes. Here at Intellectsoft, we have delivered over 600 digital solutions of different types and complexity to businesses, from startups to Fortune 500 enterprises like Mitsubishi, Harley Davidson, Melco, Intel, and many others. We have 15+ years of experience in providing business solutions for multiple industries like fintech, healthcare, construction, logistics, eCommerce, and others. Over these years, we have gathered a top-skilled team of prominent experts, including software architects. This exam will be suitable not only for solutions architects but also for any experts dealing with Google Cloud technologies.
So, an experienced solution architect should be able to listen, advise, empathize, and explain. Most solutions architects have spent at least a few years in software development. This gives them a strong understanding of the tools http://fresh25.ru/imm42.html and technologies involved in designing solutions. Five to 10 years of hands-on experience in network administration or information technology systems is common, but it varies based on what a specific company is looking for.
Technical Architect
In the context of software development, an architecture represents both the structure of the future software product and the plan of building it in order to meet client’s requirements and solve their specific problem. This definition may seem vague and generic, but only because customers’ problems are different, so they demand different solutions, usually with a unique approach. The enterprise architecture tool is designed to help solutions architects manage the transformation and risk of an organization’s IT landscape. This tool leverages technology to make decisions quickly, map designs, and manage possible outcomes and risks of the chosen solution. Looking for a way to build your skills and expertise as a solutions architect and add to your existing resume?
I am assigned to an account and I help the account manager focus on what it is they’re selling. So, those conversations basically can be very high level — like a 10,000 feet away kind of view — or a detailed technical conversation. While the development lead is responsible for their part of the solution, the SA is the proverbial one neck to choke if it doesn’t all come together right. The SA has the ultimate responsibility for making the technologies work together. As a result the SA role comes with a requisite level of responsibility for the success of the project. The Solution Architect’s role within the IT organization in devising technical solutions that tackle business challenges is fundamental.
Q: What would your recommendation be to anyone looking to pursue a career as a Solutions Architect?
They must continue to motivate the Developer Lead(s) to push through tough issues and create the solution. The solution architect role also requires being able to project into the future and consider upcoming uses. A solutions architect must view the long-term use of this product and implement scalability and adaptability into the solution for the future. A company typically needs a Solution Architect when it is on the cusp of designing, developing, or implementing a sophisticated technology solution to address a specific business issue or realize a particular goal.
Anyone applying for the role of a Solutions Architect position must have a certain set of skills, education, certifications and relevant work experience. CTO at Emizentech and a member of the Forbes technology council, Amit Samsukha, is acknowledged by the Indian tech world as an innovator and community builder. He has a well-established vocation with 12+ years of progressive experience in the technology industry. He directs all product initiatives, worldwide sales and marketing, and business enablement. He has spearheaded the journey in the e-commerce landscape for various businesses in India and the U.S.
configuration control board CCB Glossary
In smaller organizations, however, the approver and the change manager are the same people. By everyone evaluating the change from their perspective, the change control board determines if the change is worth the impact it might have on the schedule and budget of the project. The change control board is not always the last word on the subject, though. While the change control board usually has the authority, its decision is not always final and binding.

For example, an external CCB comprising users, developers and marketing people is formed to deal with changes that will impact the customer. The countryside is hilly and the topographical map, inset, names 14 short, low to medium-height mountain ranges including the Rhön, the Westerwald, the Taunus, the Vogelsberg, the Knüll and the Spessart. Forming a mid-eastern tiny projection into mostly Thuringia is the uppermost part of the Ulster, commanding the west valley side of which is the Hessian highest point, Wasserkuppe at 950m above sea level – in the Rhön. Only four years later it was clear that the terminal was already too small for the demand.
Keep Stakeholders Updated With One-Click Reports
Therefore, it is crucial that the CCB members are sufficiently equipped with information, experience, and support necessary to make the best decisions. It’s a group of people from the project team that meets regularly to consider changes to the project. Through this process of detailed examination, the change control board decides on the viability of the change request or makes recommendations accordingly. A change control board includes representatives of the relevant functional areas of the project in addition to the project manager.
After acquisition Opel by Stellantis, it is in rapid decline of production and employment. Which has also negative effect on automotive parts supplier, Continental will close a plant in Karben and cut jobs at other location in Hesse. In northern Hesse, in Baunatal, configuration control board Volkswagen AG has a large factory that manufactures spare parts, not far-away from it there is also a Daimler Truck plant, which produces an axes. Two notables oxbow lakes, the Stockstadt-Erfelder Altrhein and Lampertheimer Altrhein are in the south-west fringe. Around the turn of the 20th century, Darmstadt was one of the centres of the Jugendstil.
project management
If changes are requested, the change control board shows how those changes are managed with the least amount of disruption to the project’s plan. The importance of a change control board to a successful, high-quality project cannot be overstated. In these cases, an Emergency Change Advisory Board (eCAB) can be formed as a temporary subset of the routine CAB. The eCAB may include some or all individuals from the CAB, and this group will meet outside the normal schedule to review the necessary emergency change(s).

The Green party, a member of Hesse’s previous governing coalition with CDU, gained 8.7% (16 seats). The largest gains during the election were made by Alternative for Germany (AfD) at 13.1%. As AfD had not passed the 5% threshold in the 2013 state election, this marked its first entry into the Hessian parliament (Hessischer Landtag). The major losses of the two leading parties (whose coalition made up the federal cabinet during the election) closely mirrors the results of the 2018 state elections in Bavaria. The longest rivers in Hesse are the Eder and moreover its distributary the Fulda draining most of the north, the Lahn in the centre-west and, as to those navigable by large vessels, the Main and very broad Rhine in the south.
What is a Change Advisory Board?
The Allies of World War II destroyed the runway system with airstrikes in 1944, and the Wehrmacht blew up buildings and fuel depots in 1945, shortly before the US Army took control of the airport on 25 March 1945. After the German Instrument of Surrender, the war in Europe ended and the US Army started to build a new temporary runway at Frankfurt Airport. The southern part of the airport ground was occupied to build the Rhein-Main Air Base as an Air Force Base for the United States Air Forces in Europe. Usually, if top leaders or C-suite executives sit in the CAB, then it has highest authority. The organization’s change management policy will define the CAB’s constitution and its scope, which can include anything from proposals and deployments to changes to roles and documentation. Poor change control can significantly impact the project in terms of scope, cost, time, risk, and benefits.
- They include Air Malta, Bulgaria Air, Iran Air, Oman Air and Tunisair among others.
- The Green party, a member of Hesse’s previous governing coalition with CDU, gained 8.7% (16 seats).
- Organizations may choose to have a single CCB handling change requests across multiple projects.
- DM2 issues impacting the foundation are forwarded to the International Defense Enterprise Architecture Specification (IDEAS) Group for consideration.
- The official opening of the new Flug- und Luftschiffhafen Rhein-Main took place on 8 July 1936.
A change control board looks at change requests which are then reviewed in detail. The changes differ from the baseline requirements set at the approval of the project plan. The change control board then debates the pros and cons of a change, which is why it’s important to have a change control board that reflects all project aspects, from the team to the end-user. Larger projects that include many teams working together typically have a central change control board in addition to various change boards specific to their project area.
Configuration Control Board Configuration Management Systems Engineering
If the change is approved, the change control board will deliver a timeline followed by a testing and iteration stage. They’ll continue to meet and discuss potential problems and make sure the change stays on schedule. At every meeting, the Change Advisory Board reviews requested changes using a standard evaluation framework. That framework should consider all dimensions of the change, including service and technical components, business and customer alignment, and compliance and risk. The CAB must also look for conflicting requests—these cases in particular require CAB members to maintain holistic, business-outcomes views that don’t favor the particular team or individual seeking the change. The change control board is part of the change management planning for a project or organization.
These teams report to the central change board that has the final say on the matter. There might also be a site change board for smaller changes that only impact remote sites. Organizations may choose to have a single CCB handling change requests across multiple projects. A low-level CCB could handle lower priority change requests, for instance non-customer-facing features or changes with low/no cost impact. A higher-level CCB could tackle major change requests that have significant impact on costs or customer. The Change Control Board and the Change Advisory Board are similar organizational structures play vital roles in decision making.
Customer Service/Technical Support/Help Desk Agents
They include Air Malta, Bulgaria Air, Iran Air, Oman Air and Tunisair among others. The airships were dismantled and their huge hangars demolished on 6 May 1940 during conversion of the base to military use. Luftwaffe engineers subsequently extended the single runway, and erected hangars and other facilities for German military aircraft.

ProjectManager is work and project management software with multiple project views that allow you to work how you want. Whichever view you use, you can create one or multiple tags and filter accordingly to track project changes. Because there’s one source of project truth, both the project team and the change control board can work with the same data.
Change Control Board: Roles, Responsibilities & Processes
A Change Control Board (CCB), also known as the configuration control board, is a group of individuals, mostly found in software-related projects. The group is responsible for recommending or making decisions on requested changes to baselined work. The dashboard is good for a general overview, but when they want to zero in on something and take a closer look, one-click reports can be generated for status or portfolio reports, time, cost and more. All reports can be filtered so board members can focus on the most relevant data.
How a Change Advisory Board makes decisions
The official opening of the new Flug- und Luftschiffhafen Rhein-Main took place on 8 July 1936. Six days later, on 14 July 1936, LZ 127 Graf Zeppelin landed at the airport. In 1936, 800 tons of cargo and 58,000 passengers were transported, and in 1937 these figures increased to 70,000 passengers and 966 tons ccb definition of cargo. Wherever the change originates, capturing it is important to begin the process. Joseph is a global best practice trainer and consultant with over 14 years corporate experience. His specialties are IT Service Management, Business Process Reengineering, Cyber Resilience and Project Management.
Similar jobs
Of course, depending on the project and the organization, others might be involved. The manager leads the group, coordinates the activities and oversees all aspects of change. That is, they prioritize the change requests and lead the impact assessment of how the change affects the project. The change manager is responsible for documenting the change management process and the necessary plans to implement the change. A change log is an essential change management document that allows project managers and change control boards to keep track of the various changes that can take place during the execution of a project. This free change log template lets you list down project changes, the dates when they were made, which actions were taken and the impact of those changes.
Machine Learning: What It is, Tutorial, Definition, Types
Artificial neural networks have been used on a variety of tasks, including computer vision, speech recognition, machine translation, social network filtering, playing board and video games and medical diagnosis. The discipline of machine learning employs various approaches to teach computers to accomplish tasks where no fully satisfactory algorithm is available. In cases where vast numbers of potential answers exist, one approach is to label some of the correct answers as valid. This can then be used as training data for the computer to improve the algorithm it uses to determine correct answers. For example, to train a system for the task of digital character recognition, the MNIST dataset of handwritten digits has often been used.
This technique allows reconstruction of the inputs coming from the unknown data-generating distribution, while not being necessarily faithful to configurations that are implausible under that distribution. This replaces manual feature engineering, and allows a machine to both learn the features and use them to perform a specific task. In this sense, machine learning models strive to require as little human intervention as possible. After a data scientist designs machine learning algorithms, the computer/machine should carry out the learning process by itself, which can be realized in several different ways.
Learning from the training set
It is a rapidly growing field with wide-ranging applications in many different industries, from healthcare and finance to transportation and manufacturing. It is also likely that machine learning will continue to advance and improve, with researchers developing new algorithms and techniques to make machine learning more powerful and effective. There are a variety of machine learning algorithms available and it is very difficult and time consuming to select the most appropriate one for the problem at hand. Firstly, they can be grouped based on their learning pattern and secondly by their similarity in their function. Reinforcement machine learning is a machine learning model that is similar to supervised learning, but the algorithm isn’t trained using sample data. A sequence of successful outcomes will be reinforced to develop the best recommendation or policy for a given problem.
Machine Learning is, undoubtedly, one of the most exciting subsets of Artificial Intelligence. It completes the task of learning from data with specific inputs to the machine. It’s important to understand what makes Machine Learning work and, thus, how it can be used in the future. In some cases, machine learning can gain insight or automate decision-making in cases where humans would not be able to, Madry said. “It may not only be more efficient and less costly to have an algorithm do this, but sometimes humans just literally are not able to do it,” he said. The goal of AI is to create computer models that exhibit “intelligent behaviors” like humans, according to Boris Katz, a principal research scientist and head of the InfoLab Group at CSAIL.
Sharing the data output
Artificial neurons may have a threshold such that the signal is only sent if the aggregate signal crosses that threshold. Different layers may perform different kinds of transformations on their inputs. Signals travel from the first ai development software layer to the last layer , possibly after traversing the layers multiple times. Supervised anomaly detection techniques require a data set that has been labeled as “normal” and “abnormal” and involves training a classifier .

Machine learning is an application of artificial intelligence that uses statistical techniques to enable computers to learn and make decisions without being explicitly programmed. It is predicated on the notion that computers can learn from data, spot patterns, and make judgments with little assistance from humans. Supply chain management uses data-based predictions to help organizations forecast the amount of inventory to stock and where it should be along the supply chain.
The definitions of machine learning, AI, and deep learning
These enormous data needs used to be the reason why ANN algorithms weren’t considered to be the optimal solution to all problems in the past. However, for many applications, this need for data can now be satisfied by using pre-trained models. In case you want https://globalcloudteam.com/ to dig deeper, we recently published an article on transfer learning. This means that the prediction is not accurate and we must use the gradient descent method to find a new weight value that causes the neural network to make the correct prediction.

Robotics, gaming, and autonomous driving are a few of the fields that use reinforcement learning. For instance, IBM’s Watson platform can determine shipping container damage. Watson combines visual and systems-based data to track, report and make recommendations in real-time. The benefits of predictive maintenance extend to inventory control and management. Avoiding unplanned equipment downtime by implementing predictive maintenance helps organizations more accurately predict the need for spare parts and repairs—significantly reducing capital and operating expenses.
How does Machine Learning Work?
In 2018, a self-driving car from Uber failed to detect a pedestrian, who was killed after a collision. Attempts to use machine learning in healthcare with the IBM Watson system failed to deliver even after years of time and billions of dollars invested. The data lakehouse vendor’s purchase of the generative AI vendor will enable customers to build and train language models …
These artificial neurons loosely model the biological neurons of our brain. A deep neural network can “think” better when it has this level of context. For example, a maps app powered by an RNN can “remember” when traffic tends to get worse. It can then use this knowledge to recommend an alternate route when you’re about to get caught in rush-hour traffic.
Training models
Today, machine learning enables data scientists to use clustering and classification algorithms to group customers into personas based on specific variations. These personas consider customer differences across multiple dimensions such as demographics, browsing behavior, and affinity. Connecting these traits to patterns of purchasing behavior enables data-savvy companies to roll out highly personalized marketing campaigns that are more effective at boosting sales than generalized campaigns are. When getting started with machine learning, developers will rely on their knowledge of statistics, probability, and calculus to most successfully create models that learn over time.
- Generalization in this context is the ability of a learning machine to perform accurately on new, unseen examples/tasks after having experienced a learning data set.
- Unlike supervised learning, reinforcement learning lacks labeled data, and the agents learn via experiences only.
- What are some concrete ways in which machine learning and AI optimize industrial operations?
- For example, they can consider variations in the point of view, illumination, scale, or volume of clutter in the image and offset these issues to deliver the most relevant, high-quality insights.
- Connecting these traits to patterns of purchasing behavior enables data-savvy companies to roll out highly personalized marketing campaigns that are more effective at boosting sales than generalized campaigns are.
What Is Customized Utility Development? Steps, Advantages Information 2024
Custom software addresses users’ specific wants more comprehensively than conventional off-the-shelf packages. Our staff at Seven Peaks Software will concentrate on product improvement, product life-cycle, and software improvement to create custom-made cell and internet apps. We may also present software QA testing, cloud solutions, and other digital transformation services.
Involve key stakeholders within the necessities gathering course of to collect diverse perspectives and needs. In case of T&M with a cap, an upper limit on the costs gets established to maintain the budget beneath strict management. Supply chain software program is used to automate and coordinate all actions related with product motion from sourcing/manufacturing to distribution. The resolution permits investment professionals to securely commerce bonds, monitor their portfolios, and automatically generate financial reports. By increasing its net service with handy self-service choices, the Customer capitalized on greater investor satisfaction. Our experience spans all main applied sciences and platforms, and advances to progressive technology developments.
The Highest 10 Apps For Buying And Selling Secondhand Items
A software developer that helps teams connect successfully with customers using enterprise-class communication tools such as Zoom and Skype for Business. A software development firm can only be thought-about a top-notch development firm by the applications it creates and the success rate the company has achieved. A software improvement company with strong technical expertise and leadership qualities has a strong project portfolio.
Don’t miss to faucet into the growing potential of customized software options and give your enterprise an exceptional edge. A crucial part of our software program development as a service is analyzing the project requirements. Our professional builders decide the scope of the project and plan the event process. ScienceSoft’s staff undertook the development of our product from scratch and showed deep experience within the .Net environment and AWS and Azure providers.

With 5.5 years of common expertise amongst all our team members, we primarily hire senior engineers, to make sure the very best quality with consistent supply of initiatives. Our senior worldwide design team has in depth UX experience in designing web and cellular applications with modern person interface and consumer expertise design for Web, iOS, and Android using our confirmed UX technique. Our quality assurance process consists of our high quality assurance staff engaged on the check strategy, person testing, QA testing, as nicely as dedicated testing teams for each handbook and automated testing. Strong communication skills are essential to understanding customer targets and necessities. With the right communication abilities and project knowledge, software program improvement corporations can carefully design and develop software that provides worth to their enterprise. Regular buyer communication is crucial for long-term customer relationships.
Comparatively, customized software applications aren’t immediately out there from a producer, as a result of they don’t meet the wants of varied businesses/industries. Instead, customized software program must be planned, developed, and supported for a particular firm. Maintenance is amongst the advantages of custom software functions, as the event company will take care of the project even after release.
Customized Utility Development [an Ultimate Information Of 2024]
ScienceSoft’s staff is responsive, skilled, and easy to speak with. Our licensed PMs and Scrum masters have experience with customized growth initiatives of various scope and complexity, including large-scale tasks for Fortune 500 firms. ScienceSoft designed and developed a patient portal with telemedicine functionality for an NYC-based healthcare supplier. Three months after the launch, the EHR-integrated solution has attracted over 1,500 sufferers. Despite the clear advantages of tailor-made software program, some firms should still doubt the excessive ROI of customized development for his or her case. Our staff can conduct a comprehensive feasibility study that can help you perceive the anticipated worth of custom improvement for your small business.
- Our turn key tasks allow for a fixed-price managed delivery of a particular scope of labor.
- This entails a concerted effort to learn concerning the client’s distinctive wants and aims so that you may tailor your service accordingly.
- The agile methodology helps to handle a project by breaking it down into several phases.
- Scalability is considered one of the deciding elements when thinking about expertise for your small business.
- The third step in customized software improvement is to actually build the appliance on a low-code, no-code platform.
The third step in custom software improvement is to truly construct the applying on a low-code, no-code platform. This is a step that relies closely on the expertise of the business consumer since they know intimately how each request flows, what is needed, and the method to bring about resolution. Both ideas concentrate on building apps with a narrow set of requirements based mostly on the particular wants of a given set of customers. Low-code, no-code citizen development platforms have encouraged the rise of a new class of citizen development.
Award-winning Custom Software Improvement Firm
These important tools help businesses create geolocation service apps that real-time monitoring of autos and objects with excessive accuracy, handy navigation, and error-free info. That means, transferring firms can be more environment friendly, get pleasure from higher security, and assist construct belief with their prospects. As the best customized software https://www.globalcloudteam.com/ program growth firm in USA, we first build an MVP to check the efficiency of your product. We ensure the implementation of rigorous testing techniques, acquire continuous suggestions to meet user necessities and ship a user-friendly and intuitive software answer. With a spreadsheet or an off-the-shelf software package deal, a person can get benefits shortly.
Our improvement practices streamline and optimize numerous enterprise processes, similar to value management and clinical determination help, adhering to the unique necessities of various industrial domains.
As a software improvement outsourcing firm, we design software solutions for the aviation industry by integrating flawless engineering design. The custom solution ensures complete efficiency and precision

We helped the model in the profitable launch of seven KFC meals supply apps in a single yr, additional fortifying their international digital presence. Large, integrated options that serve as centralized storage for company knowledge and a supply of insights or enable a seamless circulate of processes and knowledge between departments, e.g., ERP, SCM. We provide options to keep up ongoing security of the IT environment and enterprise continuity amid emergency events. We develop desktop apps for Mac, Windows and Linux in C++/Qt, .NET and Python programming languages. Experts in .NET, Java, PHP, C++, Python, Golang, JavaScript, iOS, Android, and other programming languages.
Requirements evaluation and planning is due to this fact crucial part of the overall development process. In-depth evaluation is essential for improvement firms to meet all customer needs. In this section, buyer targets are translated into plans so that the 2 visions can collide. Collecting all this info helps software improvement corporations decide if you are a good fit for his or her project.
Finally, remember to ask questions about the app’s security, who’s answerable for the ongoing support and upkeep of the applying, and who retains possession of the code. These questions are important for the long-term success of your new utility. When the pandemic struck the world in 2020, it forced officials to shut the physical lecture rooms and educators to search out different methods to ship schooling and ensure their students’ safety.
What Are The Highest 14 Examples Of Custom Software Development?
The buyer’s requirements should be documented and verified by both parties before proceeding to the next stage. Customer necessities are recorded in SRS (Software Requirements Specification) paperwork, upon which merchandise are designed and developed. Planning your requirements additionally helps make positive that there are no misunderstandings.
It involves designing, developing, and deploying solutions tailored to an organisation’s distinctive wants. As a half of our custom-made software growth companies, we start by understanding the particular define custom software wants, objectives, and functionalities required for designing your custom software. As one of the most sought-after customized software development companies, we analyze your corporation wants,
It provides trendy, easy-to-use software options that make managing and organizing knowledge, duties, and person providers more environment friendly. Once a growth company understands what it must build, it wants to consider tips on how to proceed with it. The internal structure of all modules of the software is described within the SRS documentation.
Let’s take a extra in-depth have a look at what customised options are and the method it helps businesses succeed. The price of custom software growth tasks varies significantly relying on the size and complexity of the project, the technologies used, and extra. While upfront costs are sometimes greater than those of off-the-shelf software, over time, the funding in customized software usually pays off.
What is Defect Density? Formula to calculate with Example
Yamanaka, A., McReynolds, K. & Voorhees, P. W. Phase field crystal simulation of grain boundary motion, grain rotation and dislocation reactions in a BCC bicrystal. & Maugin, G. A. Nonsingular stress and strain definition of defect density fields of dislocations and disclinations in first strain gradient elasticity. Cai, W., Arsenlis, A., Weinberger, C. & Bulatov, V. A non-singular continuum theory of dislocations. Solids 54, 561–587 .

The Secret to Releasing Quality Products with Fewer Testing Resources Test Strategy With businesses experiencing setbacks, building a product that stands out amongst your competition is critical. While layoffs or budget freezes can leave you with fewer resources, customers expect that their money gets them a quality product, especially in a downturn. What is delta testing and how are tech leaders using it to deliver customer insights throughout agile development? This guide has all the answers. Let us take an example of a software application that has been integrated with three modules and the number of bugs the tester found in each module.
Test Cost-Effectiveness and Defect Density: A Case Study on the Android Platform
Higher defect densities may indicate that a product has more issues or bugs, while lower defect densities may indicate that a product is of higher quality. Below relevant defect densities, many materials at the microstructural level have properties 10–100 times better than their bulk counterparts. Parameters such as strength, piezoelectricity, fatigue strength, and many others exhibit this behavior. Outside the microworld, however, efforts to exploit these properties directly have been stymied by the challenges of identifying defect-free particles and then combining them in sufficient numbers to be useful.

In the glossary we gather the main specialized terms that are frequently used in the working process. All meanings are written according to their generally accepted international interpretation. For convenience, you can use the search bar to simplify and speed up the search process. A more detailed analysis would require finding a solution for the amplitudes’ profile at defects, which goes beyond the goals of this investigation and will be addressed in future work.
square lattice PFC
For example, if 10 out of 200 tested units are defective, the defect rate is 10 divided by 200, or 5 percent. Defect rate is often stated in terms of defects per million. Nejad, M. R., Doostmohammadi, A. & Yeomans, J. M. Memory effects, arches and polar defect ordering at the cross-over from wet to dry active nematics. Soft Matter 17, 2500–2511 . Topological fine structure of smectic grain boundaries and tetratic disclination lines within three-dimensional smectic liquid crystals.

With the assistance of this metric, software engineers, developer, testers and more can measure the testing effectiveness and differentiate defects in components or software modules. The use of defect density is inconsiderable in many ways. However, once developers set up common defects, they can use this model to predict the remaining defects.
Is Vector a legit company?
It’s found by dividing the total number of defects found by the number of units. For example, if 30 units are produced and a total of 60 defects have been found, the DPU equals 2. Defect density is considered one of the most efficient testing techniques in the overall process of the software development process. While this practice is considered unnecessary by some software engineers, but it is still revered as the best way to identify bugs and errors in software. Above all, the efficiency and performance of the software remain the biggest factor that affects the defect density process.
- Is the usual scaling property of the delta function taking Ψ as input, apart from the sign of D carrying information of the charge qα of the topological defects.
- Defect density also makes it easier for developers to identify components prone to defects in the future.
- It includes a development procedure for calculating the number of flaws, which allows developers to identify weak regions that need to be thoroughly tested.
- Software is tested based on its quality, scalability, features, security, and performance, including other essential elements.
- When approaching the solid–liquid coexistence limit, analogies between the dislocation core size and the extensions of order-disordered interfaces have been found.
It includes a development procedure for calculating the number of flaws, which allows developers to identify weak regions that need to be thoroughly tested. As a consequence, testers can focus on the proper areas and provide the highest return on investment with little resources. The testing team will be able to hire a third-party inspection crew for re-engineering and substitutions. It is used to determine the number of software flaws. It is important to perform an optimization of the electrode placement in the design of the physical device as it plays a role in reducing the current crowding.
What means defect density for testers.
With the assistance of defect density, one can differentiate defects in components/software modules. Defect Density is the number of confirmed defects detected in the software or a component during a defined period of development or operation, divided by the size of the software. It is one such process that enables one to decide https://www.globalcloudteam.com/ if a piece of software is ready to be released. The number of defects identified in a component or system divided by the size of the component or system (expressed in standard measurement terms, e.g., lines-of-code, number of classes or function points). DPU measures the average number of defects per every product unit.

Every software is assessed for quality, scalability, functionality, security, and performance, as well as other important factors. In a system testing procedure, it’s typical to find flaws and faults. Developers must, however, verify that they are addressed before releasing it to end-users. This is because correcting an inaccuracy at an initial point is far less expensive than correcting it later.
How many standard deviations is 1.33 Cpk?
For example, the number of particles per unit area of size greater than some threshold value goes roughly as the inverse area subtended by that particle. Collect the raw material, i.e., testers will require the total number of defects detected while developing the software product. Also, identifying defect prone components is made easy through defect density, which allows the testers to focus the limited resources into areas with the highest potential return on the investment. This further helps organisations and their businesses reach great heights of success, as they are able to deliver software and applications that are secure, safe, bug free and more. To measure defect density, you need to have the data on the number of defective units of a single product, as well as the total number of units produced. To find the density, divide the number of defective units by the total number of units produced.
Before the release of the product, one can determine whether the testing is sufficient. The type of defects taken into account for the calculation. Zhou, C., Biner, S. B.
bcc lattice PFC
Time duration which is considered for defect density calculation. Calculate the average number of defects/ Functional area or line of code . Explore the possibility to hire a dedicated R&D team that helps your company to scale product development.
The Method To Construct A Calendar App In 2023 Complete Guide For Startups
You should choose the technologies that will ensure the flexibleness of your app within the near future. Various sectors can create an in-app calendar to boost their software values to the customers. Calendars are created with myriads of shade schemes and interfaces. However, the ultimate http://unibassein.ru/art/otkazhites_arsenal_barselona_liga_chempionov/ function of the calendar is always the identical – to remind the users of dates and days to assist them manage their routine. There are a lot of libraries on GitHub that can be used for calendar app development.
Provide admin controls to manage integrations with platforms and exterior calendars. It consists of organising API connections, guaranteeing information is exchanged smoothly, and troubleshooting integration points. If you wish to develop a calendar app for your fitness and wellness business, you want to know it’s a premium alternative to spice up users’ engagement.
This is how others can click on on the link to attend a gathering with you. Calendar apps are used to boost productiveness and Time Block is one prime instance of this. Schedule your timings to work on essential tasks as they allow you to complete them in these blocks.
- They can add or remove them, reset their passwords and execute permissions.
- In the above blog, we’ve given many cool calendar app concepts, options, and functionalities that you could add to your app.
- Include a robust search and filter system that helps users discover particular events shortly inside their calendars.
- Users can manage their daily, weekly, and month-to-month calendars in a single location, giving them a complete perspective of their schedules.
- Developing a primary calendar app with some easy options is not tough.
Emizentech has all these features to assist enterprise owners and entrepreneurs who need assistance staying organized and creating exceptional apps. Perhaps probably the most promising performance that digital calendars at present present is utilizing natural language to add and edit calendar entries. Scheduling apps like Calendar and Voice Calendar have efficiently applied this characteristic.
We will explore eight industries the place we can develop a calendar app to enhance their services. The Calendar App is a revolutionary tool that revolutionizes time administration and scheduling. It was developed to simplify private and skilled organization.
Influence Of Technology On Route Management Methods
In this section, we now have compiled a singular desk involving the ten best calendar apps you must know. Transform your app improvement expertise to develop a calendar app that can stand the check of time. To handle your resources correctly, enter them into your online calendar.
On Telegram, for example, users can send scheduled messages by holding the Send button in a chat and selecting Schedule Message. The message will then be sent automatically at the specified time. Telegram users can use their Saved Messages chat to turn deliberate messages into reminders. The finest calendar app for iPhone or Android supplies priceless perception into user behavior. This data-driven technique permits for continuous enchancment and customization according to person needs. Emizentech is a software improvement company that has successfully spearheaded quite a few home and worldwide cellular app development projects.
Google and Apple present a lot of APIs for integrating into a calendar utility. In a parking app, users can discover a place by reserving the time and date using the in-app calendar. Users can schedule their rides and would obtain a reminder when the driver arrives at the spot. Agile improvement is crucial to remain versatile and responsive throughout the whole development cycle. Regular sprints and steady suggestions loops will enable the event process to adapt and evolve with altering requirements.
To finish, we’ll share with you a couple of extra tips to ensure that your app provides an excellent consumer expertise. So far, we’ve explored use circumstances of in-app calendar functionality associated to daily planners, productivity apps, and task managers. In order to avoid overlapping events, we implemented augmented reality mode. To use this characteristic, users hold the app over their Slice Planner pocket book and the app notifies of any overlapping occasions. For example, Uber Freight has plenty of cool options based on the in-app calendar.
Ui Element & Picture Loading Libraries
Apple and Google provide a lot of APIs to combine right into a calendar app. Please, note, that the tech stack offered under is approximate. The last tools all the time rely on your project requirements and enterprise targets.
Gain the aggressive edge and increase the safety of your calendar occasions and different scheduled tasks by utilizing the 3D contact, darkish theme, or face recognition. Moreover, using geo-location in occasions also improves total work efficiency. Users can draw traces round necessary notes so the Slice Planner app will capture them. This permits customers to save heaps of, share, and fasten notes to their calendar occasions. Specifically, we constructed optical character recognition software program powered by Google Cloud Vision, as this software program accurately recognizes occasion titles.
Dev Technosys excels in app growth, guaranteeing revolutionary, scalable, and user-friendly options. Our experience, dedication to quality, and client-focused method make us a perfect alternative for calendar app development. Implement a system of reminders to tell customers about upcoming events. Customizable notifications, corresponding to email or push notifications, can improve person engagement and ensure important occasions aren’t missed. In-app calendars are easy to make use of and accessible, providing a seamless guest expertise. So, choosing to develop a calendar app is exceptionally significant if you would like to spend cash on journey app growth.
Choose From A Native, Android/ios, Or A Cross-platform App
The hospitality business relies on environment friendly administration to coordinate occasions, reservations and employees shifts. Statista found that eating places and resorts that carried out in-app calendars saw a discount of 25% in reserving errors and a rise of 20% in buyer satisfaction. Come with us to embrace innovation, discover the world of APIs and harness the facility of user-centric design. We will ensure that your calendar app does not simply hold observe of dates but in addition revolutionizes how users manage their lives sooner or later.
For example, your calendar app is ready to make the most of the Force Touch or 3D Touch. The UI/UX design of the calendar app is important to achieve recognition from individuals. A user-friendly and engaging interface is the requisite of a calendar app. An online calendar app may give you notifications for all the activities taking place. Suppose you’re a skilled who has to arrange and attend a lot of conferences in a day.
This growth can be attributed to the enhanced options, seamless system integration, and evolving needs of the dynamic person base. Here, we’ve talked about a few of the components that you have to consider when making a calendar app. This makes it straightforward to maneuver events from one group to a different with out including them by hand. From new bookings and cancellations to new members in a meet, you can have a glance at all actions essential to customers from the second they start utilizing the app. Explore entry through Facebook or Google, which supply basic functionality with the power to customize through JavaScript. The calendar in the well being app is used to remind you to take your drugs, schedule a doctor’s appointment, or have tests ready.
Apis To Construct A Calendar App
A calendar app would possibly use sensitive private information, due to this fact, application security is important. Emizentech has extensive expertise in developing safe web and mobile apps. Sometimes, planning an occasion or activity is the hardest a half of scheduling it. Some good calendar apps have options for planning events that mechanically pull info from the sentences you type. This good assembly scheduler cuts down on time it takes to plan an event and set a date and time. Travel, time, and dates are interrelated with each other but maintaining all of them collectively on monitor is a troublesome task.
Introduction Of Calendar App
You may create an occasion and invite others from your contacts or email addresses. FaceTime videoconferencing capabilities cannot be added to a Mac. After inviting people to a gathering, you may also view their responses. Since I had trouble booking a cab, the transportation industry has given in-app integration much thought. But there could be plenty of customers like me who compelled a business to add the feature.
Integrate Bitbucket & Jenkins Connect Jenkins And Bitbucket And By Bharathiraja Ampersand Academy
If you’re using Jenkins for continuous integration, this migration can be complex and even frustrating. After spending several hours on plugins and Atlassian documentation with no success, I decided to create this complete guide that will help you navigate this transition easily. Install the Bitbucket Post Webhooks plugin and navigate to the repository settings to configure the triggers.
- Once they’re linked, users can then complete the authorization course of to perform Jenkins actions in Bitbucket.
- You can both do this manually by cloning the repository and pushing it to a model new Bitbucket Cloud repository or use Bitbucket’s built-in migration instruments.
- After a second, your Jenkins instance will seem within the listing of linked purposes.
- Now with the Jenkins setup for Bitbucket, we are ready to test the entire configuration.
- DevOps performs a very important function in utility growth.
Add create your super simple pipeline that builds the branch or just print the hello world message. Secondly, create a Jenkins Pipeline that checks out and builds the code. The plugin streamlines the whole configuration course of and removes the need for a number of plugins to attain the identical workflow. Since 1.1.5 Bitbucket routinely injects the payload received by Bitbucket into the build. You can catch the payload to process it accordingly by way of the environmental variable $BITBUCKET_PAYLOAD. Finally, the absence of errors (like pink messages underneath repo url input) implies that the process had success.
Prior to Bitbucket Branch Source 2.1.1, the one workaround is to configure every repository hook manually in Bitbucket Server. However the Bitbucket REST API can be used to facilitate that course of, have a look at the article Generate webhooks in Bitbucket Server by way of REST API for Pipeline Multibranch. This is the really helpful, faster, easiest configuration.
Configuration In Bitbucket Server
Once you’ve added a Bitbucket Server instance to Jenkins, customers will be succesful of select it when creating a job. This will make it easier for them to pick the repo to be cloned. They’ll additionally be able to select the Bitbucket Server construct trigger to routinely create a webhook. When adding a Bitbucket Server occasion you have to add a minimal of one Bitbucket Server HTTP entry token that’s configured with project admin permissions. Doing this permits users to mechanically arrange build triggers when creating a Jenkins job.
Then click the Create repository button to create a repo. And set off a job automatically in Jenkins when a new code is committed in Bitbucket. To learn how to install and configure this integration, and the means to create your first pipeline, watch this video. Bitbucket Server is a Git repository administration solution designed for professional teams. It’s a half of the Atlassian product household together with Jira, Confluence, and many extra instruments designed to help teams unleash their full potential.
Configuration In Jenkins
Update any Bitbucket-specific triggers to be compatible with Bitbucket Cloud. Add your Bitbucket Cloud credentials using ‘x-token-auth’ because the username and the Repository Access Token as the password. Please have a look at Bitbucket Webhooks Troubleshooting to troubleshoot points with these options. Click the check connection to see if it triggers the message. Firstly, we need to install the required Jenkins plugins.
Once you logged in, then click on the Create repository button like within the picture. Register and log in to BitBucket using the given hyperlink. Create New Job in Jenkins and connect BitBucket Repo using the BitBucket credentials. Previously I really have written a tutorial for Installing Jenkins.
For instructions on linking with Jenkins, see the documentation for the Bitbucket Server integration plugin for Jenkins on plugins.jenkins.io. Push code to Jenkins when new code is committed using BitBucket webhooks. The objective of this tutorial is, how to join Jenkins and BitBucket. Whenever a code is changed in BitBucket Repo, Jenkins automatically will create a new build course of.
Bitbucket Cloud Usage
Once they’re linked, customers can then complete the authorization process to perform Jenkins actions in Bitbucket. Configure your Bitbucket repository with a Webhook, using URL JENKINS_URL/bitbucket-hook/ (no want for credentials but do keep in mind the trailing slash). App passwords are substitute passwords for a consumer account which you can use for scripts and integrating tools to keep away from putting your actual password into configuration files. Select the triggers for the notifications., For instance, it is sensible to sell “On push“.
It exposes a single URI endpoint you could add as a WebHook inside every Bitbucket project you want to combine with. This single endpoint receives a full information payload from Bitbucket upon push (see their documentation), triggering suitable jobs to build primarily based on changed repository/branch. At second I’m attempting to create connection from jenkins to my bitbucket repository, using the git plugin that I’ve put in in jenkins.
In DevOps, we are going to use Git as a version management system. Integrated CI/CD enables you to create a link between Bitbucket Data Center and Jenkins, unlocking a range of advantages. One vital change is Atlassian’s determination to discontinue on-premises help, making Software as a Service (SaaS) the only choice. This has led many teams to consider migrating from Bitbucket Server to Bitbucket Cloud.
Run a take a look at build to make sure that every thing is about up appropriately. Make a code change within the Bitbucket Cloud repository to verify if it triggers a Jenkins build as anticipated. The first step is to migrate your repository from Bitbucket Server to Bitbucket Cloud. You can either do that manually by cloning the repository and pushing it to a new Bitbucket Cloud repository or use Bitbucket’s built-in migration instruments.
other tools like Sourcetree and Bamboo. Once a project is saved, it mechanically listens for events – generally sent by webhooks – on the endpoint /bitbucket-scmsource-hook/notify. The Bitbucket Branch Source plugin supplies https://www.ranch.by/natural-horsemanship/?ysclid=lm3r4oh5j1410165615 assist for integration of Bitbucket with multibranch project corresponding to Pipeline Multibranch. The API listens for notification to the endpoint /bitbucket-scmsource-hook/notify.
Install The Plugin
Now with the Jenkins setup for Bitbucket, we are prepared to check the whole configuration. App passwords are designed for use for a single objective with restricted permissions, so they do not require two-step verification (2SV). This means app passwords can be used by users with 2SV make API calls to their Bitbucket account, and to integrate Bitbucket with
Integrated CI/CD enables you to create a link between Bitbucket Data Center and Server and Jenkins, unlocking a range of benefits. Bitbucket can receive construct statuses, test outcomes, and other feedback from Jenkins, and display it in context the place it matters most. In Jenkins, you can pick a Bitbucket repository and checkout its sources with out specifying additional credentials. In this tutorial, you will learn how to connect Bitbucket and Jenkins. And set off the construct when a code is modified/ committed/ modified in the Bitbucket repository. DevOps performs a very important position in utility development.
The “unfastened matching” relies on the host name and paths of the projects matching. The older-style HTTP POSTs from Bitbucket are additionally supported however deprecated.
Jenkins will then mechanically find, handle, and execute these Pipelines. Bitbucket Server situations are added and configured at the system degree. Once they’re added users can select them from the SCM when making a Jenkins job. You must add at least one Bitbucket Server occasion to Jenkins. We’re collecting feedback at issues.jenkins-ci.org. Head there to see what points have been created, or create a model new concern using the part atlassian-bitbucket-server-integration-plugin.
Outsourcing Vs Outstaffing: Choosing The Proper Method For Your Business
It’s essential to recognize that the choice between outstaffing and outsourcing isn’t always binary; a hybrid approach can usually yield substantial benefits. A hybrid model that mixes components of outstaffing and outsourcing allows firms to leverage the strengths of each while mitigating their respective drawbacks. By strategically blending these approaches, businesses can preserve a core in-house group while accessing specialised external expertise for specific initiatives or tasks. This amalgamation offers the pliability to scale resources up or down as wanted, ensuring efficient administration of numerous projects with out sacrificing control or incurring extreme costs. At the stage where you’ve understood the subtle differences between outsourcing and outstaffing, you can also make the right choice to optimize your tech tasks and drive enterprise success.
For this cause, we now have created an analytical guide that explains what outsourcing and outstaffing is and what the primary variations are between them. This article may even assist you figure out which model best fits your corporation needs and how to discover high-quality collaboration partners http://zoshenko.ru/proizvedenia.html?ysclid=lfb5wd7z7i620678279 to outsource your IT initiatives. Outstaffing is a business structure in which a enterprise contracts skilled providers to an outsourcing firm. Outstaffing firms present staff and sources to other corporations, typically briefly.
When working with the remote team, you may have to trust them with your documentation, software, and tasks. Be certain to include required security measures when hiring an outstaffing firm. On the opposite hand, outstaffing is if you hire workers inside your personal company who specialize in certain areas corresponding to advertising or gross sales. Outstaffing provides you more control over how your business operates as a outcome of these workers report on to you and work carefully with other departments within your group. This might help with productiveness and communication amongst staff whereas also providing better customer service since everyone is working collectively in course of a standard goal. In this case, your IT services vendor can quote you what it’s going to price to work with their IT assets for the duration of your project.
Advantages Of Outstaffing
Depending in your company’s wants and resources, you must use any mannequin. However, as a basic rule of thumb, while small companies with internal groups benefit more from hiring outsiders, massive projects name for outsourcing. At ProCoders, we often ask our clients to think hard in regards to the type of outstaff initiatives wanted.
Do you may have the flexibility to let an outdoor vendor take the every day reins of your IT improvement, even if it is only for a project? If the answer to both of those questions isn’t any, you should most likely contemplate the long-term control you’ll get with outstaffing. A excellent instance of outstaffing is Procoders’ collaboration with AxisPoint/VSimple. When AxisPoint could not discover enough local engineers of their house state of Kentucky, they reached out to ProCoders for help. ProCoders answered the call with an IT Staff Augmentation Services proposal that allowed the CTO management team at AxisPoint to handle the programmers ProCoders offered immediately. This way, AxisPoint/VSimple saved both money and time on hiring.
When To Outstaff?
With this flexibility, firms may continue to function rapidly and economically. Since we’ve years of outsourcing expertise, we all know the way to arrange a clean work process remotely. Take a have a glance at our portfolio and see the tasks that we have carried out efficiently. On the other hand, if you need to temporarily increase your internal IT group, one of the simplest ways to do it’s to rent app builders or an entire employees. For instance, if you don’t have in-house expertise expertise, outsourcing is one of the best ways to go. However, your improvement partner will deal with every little thing for you.
The manager and employees know one another, and so they have established a working relationship. During outstaffing, the shopper has to construct these relationships from scratch. Having a skilled manager (with knowledge of the required language) can be useful.
Such providers can be good for both short-term and prolonged cooperation, yielding a high quality product. Outsourcing helpscompanies that don’t havemoney, time or purpose to assemble their own in-house group of builders. Such services are good for both short-term or prolonged cooperation yielding a excessive quality product. Depending in your company’s needs, you can select one or each of the models for upcoming programming tasks. Outsourcing is the process of transferring specific jobs and duties to a different firm. On the opposite hand, outstaffing is a temporary service during which corporations rent freelancers on an hourly basis for their projects/tasks.
Therefore, you understand for certain that your project is given their full attention. The outsourcing company can hold distance, handling the project on their very own and reporting progress to you all through the development cycle. Or they may be a staff participant, interacting with your specialists along the way.
Azoft Outsourcing Services
To overcome these issues, it’s critical to have sturdy safety safeguards and intensive confidentiality agreements in place. In basic, outsourcing is when you could have an idea, however there isn’t a method to implement it on your own. IT outsourcing may be complex, however it is also considered one of your company’s most necessary decisions.
Outsourcing is an incredible thought for companies that want a complete staff of IT specialists to undertake a specific project. And outstaffing is the best choice for these who want to have full management over the administration of an upcoming IT task and briefly lengthen their development team. However, the principle distinction between outsourcing and outstaffing is that outstaffing hires specialists from other firms to work on the project under the control of the enterprise owner. On the other hand, outsourcing passes the web development course of to a third agency. Outstaffing is a kind of offshore net improvement the place a customer hires a contractor from a software outsourcing firm to carry out growth tasks. In outsourcing, the consumer delegates full or partial product improvement to the outsourcing vendor’s staff.
And even more so in improvement – details and nuances can emerge that have been unimaginable to foresee. We’ll not often ship you articles to maintain you updated with the most recent software program development trends. More than a 3rd of small companies surveyed in Clutch’s 2019 evaluation outsource a business course of and greater than half have plans to outsource in the future. We are dedicated to make sure quality in detail and supply meaningful impression for customers’ enterprise and viewers.
- With outsourcing, a client company hires an entire growth staff and a supervisor who’s answerable for operating the project.
- Now that you realize the outsourcing and outstaffing distinction in software program improvement, and their pros and cons, let’s talk about when they are going to be most useful on your company.
- We will analyze the details of outsourcing vs outstaffing and clarify all of the phrases of offshore improvement.
- This permits a client to “employ” a devoted IT outstaff group member.
Instead of constructing an in-house group, many companies opt to outsource or “outstaff” their initiatives. The reply can range, depending on the project and organization. What follows is an overview of each choice and the place every makes probably the most sense. With outsourcing, a shopper firm hires a complete improvement group and a supervisor who’s liable for working the project.
To reduce these risks, efficient contingency planning and vendor administration procedures ought to be in place. Software Mind provides companies with autonomous improvement teams who manage software life cycles from ideation to release and past. For over 20 years we’ve been enriching organizations with the talent they should enhance scalability, drive dynamic growth and produce disruptive ideas to life. If you’re on the fence about your capability to outsource vs outstaff, ProCoders might help you choose the data expertise outsourcing companies. We can work along with your team as an outsourced or outstaffed useful resource. We’d love to talk to you about your wants at present and create a proposal specifically for your business needs.
Therefore, Grand View Research, Inc. calculated that the price of outsourcing and out of doors staffing would develop by 7.7 p.c per yr. By 2027, world spending will increase by $936.3 billion on account of this. In basic, cost financial savings should not be the first (much much less the only) reason for selecting outstaffing. We suggest outsourcing for secondary projects or functions and outstaffing for the primary ones, the standard of which determines the future of the complete company. However, if you’re contemplating outsourcing, you’ll have to ask yourself different questions.
Outstaffing is all about comprehensive serving of your team-scaling wants. It is when an HR companion covers for you recruiting procedures, onboarding services and post-hiring processes. Outstaffing gives you the liberty to adjust assets up or down in accordance with project needs. By modifying the quantity of employees, companies may shortly adapt to shifting market circumstances or project specifications.
Nearshore software growth is a pivotal side of contemporary business strategies, with approximately 76% of corporations opting to outsource their IT services to third-party suppliers…. You can increase your tech staff by hiring a developer from an outstaffing company and have a full team assembled to start your project. Outsourcing and workers augmentation in software improvement (outstaffing) imply totally different approaches to who and the way will do a particular tech task. And earlier than we clarify this any further, we need to provide a couple of definitions of terms we’ll use throughout the article. Looking to construct a devoted software program development team for your project?
What Are Tests of Control in Auditing?
Labor statutes like the Unfair Dismissals Act apply to employees but not contractors. (A) Except as provided in paragraphs (f)(3)(ii)(E) through (G) of this section, the trust must attach the statement to a Form 1041. The statement may be attached to either the Form 1041 that is filed for the first taxable year of the trust beginning after December 31, 1996 (1997 taxable year), or to the Form 1041 filed for the first taxable year of the trust beginning after December 31, 1997 (1998 taxable year). The statement, however, must be filed no later than the due date for filing a Form 1041 for the taxable year, plus extensions.

A trust that was in existence on August 20, 1996, and that was treated as a domestic trust on August 19, 1996, as provided in paragraph (f)(2) of this section, may elect to continue treatment as a domestic trust notwithstanding section 7701(a)(30)(E). This election is not available to a trust that was wholly-owned by its grantor under subpart E, part I, subchapter J, chapter 1, of the Code on August 20, 1996. The election is available to a trust if only a portion of the trust was treated as owned by the grantor under subpart E on August 20, 1996.
What are Tests of Controls?
The test allowed for state responsibility in
situations where a foreign power helped to coordinate the actions of an organized and
hierarchically structured armed group by equipping, financing, or training the
paramilitary force. Multivariate testing or multinomial testing is similar to A/B testing, but may test more than two versions at the same time or use more controls. Simple A/B tests are not valid for observational, quasi-experimental or other non-experimental situations – commonplace with survey data, offline data, and other, more complex phenomena. No matter the activity, all testing operations must be executed on real devices. Test Monitoring and Test Control can only be effective when tests are being run in real user conditions. Running them on emulators or simulators cannot provide 100% accurate results, and therefore QA managers won’t be able to evaluate the testing process with precision.
Any results yielded from Test Monitoring would be only partially correct, and therefore Test Control activities based on these results will not modify the test cycle for maximum productivity. In other examples, outcomes might be measured as lengths, times, percentages, and so forth. In the drug testing example, we could measure https://www.globalcloudteam.com/ the percentage of patients cured. In this case, the treatment is inferred to have no effect when the treatment group and the negative control produce the same results. Some improvement is expected in the placebo group due to the placebo effect, and this result sets the baseline upon which the treatment must improve upon.
Reperformance of Control Procedures
The statement must be attached to a Form 1041 that is filed no later than October 15, 1999. Reliable means that internal control can detect major kinds of risks that could materially affect the financial statements. And in order to assess, the auditor needs to design internal control testing on those significant control and make a conclusion. So, during the planning stage auditor is required by the standard to obtain an understanding of the client’s internal control over financial reporting. Yet, the auditor is not required to test all of those internal controls, the test of controls. The auditor is normally focused mainly on internal control over financial reporting as it mater to the financial report that they are auditing.
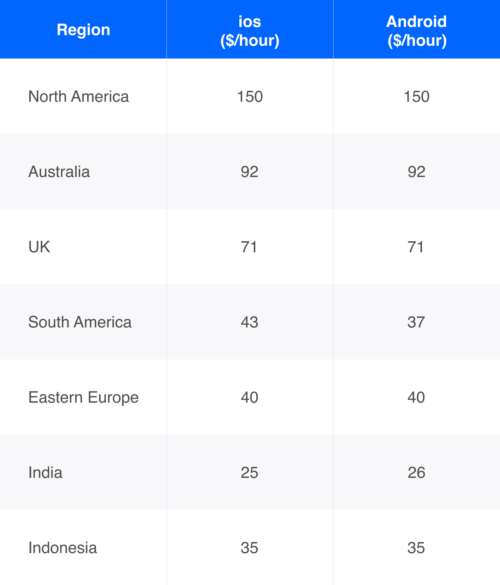
Where there are only two possible outcomes, e.g. positive or negative, if the treatment group and the negative control both produce a negative result, it can be inferred that the treatment had no effect. If the treatment group and the negative control both produce a positive result, it can be inferred that a confounding variable is involved in the phenomenon under study, and the positive results are not solely due to the treatment. The control test, also known as the irresistible-impulse test, is a legal test used in criminal law to determine if a person is criminally responsible for their actions. This test holds that a person is not responsible for their actions if they were unable to control their behavior due to a mental disease or defect. A control test is a way to determine if someone is responsible for a criminal act they committed. It is used in some places to decide if a person’s mental illness prevented them from controlling their behavior.
Curated for all your Testing Needs
The aim of tests of control in auditing is to determine whether these internal controls are sufficient to detect or prevent risks of material misstatements. A robust internal control system is essential for businesses to keep their financial records accurate. A test of controls involves many similar audit procedures to a test of detail, but the outcomes are different. While a test of controls supports control risk assessment, a test of details is performed to support the overall audit opinion of a company’s balance sheet and accompanying transactions.
While this does not ensure that there are no differences between the groups, it ensures that the differences are distributed equally, thus correcting for systematic errors. For example, to assess a new test’s ability to detect a disease control test definition (its sensitivity), then we can compare it against a different test that is already known to work. The well-established test is a positive control since we already know that the answer to the question (whether the test works) is yes.
A/B testing
In the case of a trust created pursuant to the terms of a will probated within the United States (other than an ancillary probate), if all fiduciaries of the trust have been qualified as trustees of the trust by a court within the United States, the trust meets the court test. Thus, for purposes of the court test, the United States includes only the States and the District of Columbia. Accordingly, a court within a territory or possession of the United States or within a foreign country is not a court within the United States. Test of control is one of the important approaches that is used by auditors to reduce the workload or reduce the number of sampling that the auditor will select during the substantive test or dest of detail.
- Governments should review their practices,
regulations and laws to consider restitution as an available sentencing option in
criminal cases, in addition to other criminal sanctions. - If the groups show the same effect, then the treatment was not responsible for the improvement (because the same number of patients were cured in the absence of the treatment).
- The decision whether to test the control or not is after the auditor obtains an understanding of the client’s internal control and concludes that they might not be able to test the control.
- The statement must be attached to the plan’s information return that is filed no later than the due date for filing the plan’s information return for the first plan year beginning after December 31, 1997, plus extensions.
These examples are programmatically compiled from various online sources to illustrate current usage of the word ‘control.’ Any opinions expressed in the examples do not represent those of Merriam-Webster or its editors. Conduct, manage, control, direct mean to use one’s powers to lead, guide, or dominate. The frequency with which data should be collected for monitoring purposes depends on the nature of the project. For example, if the project is slated to be completed in one month, then it makes sense to collect monitoring data weekly.
The Role of Real Devices in Test Monitoring and Test Control
The election provided by this paragraph (f) to be treated as a domestic trust may only be revoked with the consent of the Commissioner. However, this paragraph (c)(4)(ii) will not apply if the trust instrument provides that the trust will migrate from the United States only in the case of foreign invasion of the United States or widespread confiscation or nationalization of property in the United States. The term primary supervision means that a court has or would have the authority to determine substantially all issues regarding the administration of the entire trust. A court may have primary supervision under this paragraph (c)(3)(iv) notwithstanding the fact that another court has jurisdiction over a trustee, a beneficiary, or trust property. (2) A trust is a United States person for purposes of the Internal Revenue Code (Code) on any day that the trust meets both the court test and the control test. For purposes of the regulations in this chapter, the term domestic trust means a trust that is a United States person.
Tests of control are only performed when the auditor believes that the control risk is low, enabling them to verify this assessment. However, a test of details is almost always required to obtain sufficient audit evidence. Reperformance is another audit procedure that auditors can use as a part of test of controls.
Contract of Service Vs. Contract for Service
It typically consists of auditors’ independent execution of procedures or controls that the client performs as a part of its internal control system. For instance, it involves auditors reperforming the bank reconciliation process to check for any inefficiencies in the process. Reperformance is the most reliable form of audit evidence that auditors can obtain.
